OAuth Authorization Code Flow with PKCE
Configure the Client
UserVoice follows the OAuth2 specification for authenticating access to its APIs. For public clients, such as a Native App, it is highly recommended to authenticate using the Authorization Code Grant flow with PKCE.
To configure your application to use the UserVoice Idea Collection API please follow the steps below:
From Admin Settings > Integrations, create a new API Key to be used by your app:
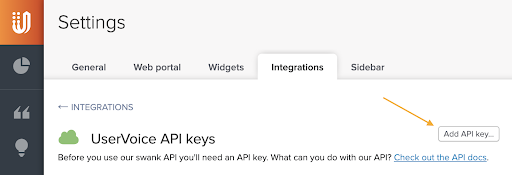
Give your API Key a name and specify your Redirect URI (where your client Auth resides) as the Callback URL:
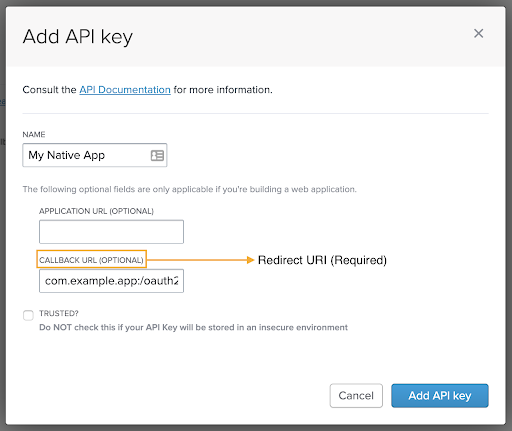
NOTE: Read more about Redirect URIs for Native Apps in OAuth 2.0 for Native Apps (Page 8). NOTE: It is not necessary to select the “Trusted?” option for clients using the
/end_users/API. If you do, do not expose your key.From your application, request an Authorization Code using the API key created above:
https://<YOUR_SUBDOMAIN>.uservoice.com/api/v2/oauth/auth?client_id=<YOUR_API_KEY>&redirect_uri=<YOUR_REDIRECT_URI>&response_type=code&code_verifier=<YOUR_ENCODED_VERIFIER>&code_challenge_method=S256NOTE: The
code_verifierandcode_challenge_methodparams are optional. UserVoice only currently supports S256 as thecode_challenge_method. Learn more about PKCE.The GET request above returns a redirect to a UserVoice Sign In page. Once the user successfully authenticates, they will be directed back to the Redirect URI with a query parameter containing the authorization code:
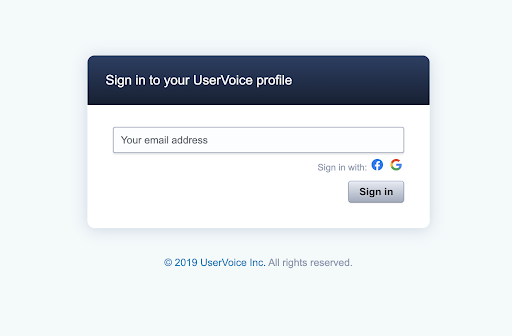
Example Redirect:
https://<YOUR_REDIRECT_URI>?code=<UV_AUTH_CODE>With the acquired Authorization Code, submit a POST request to obtain a bearer token:
http://<YOUR_SUBDOMAIN>.uservoice.com/api/v2/oauth/token?grant_type=authorization_code&client_id=<YOUR_API_KEY>&code=<YOUR_DECODED_VERIFIER>Example Response:
{ "access_token": "<YOUR_TOKEN>" }Include this token in the Authorization header of every API request:
Authorization: Bearer <YOUR_TOKEN>

